What is the role of an ICT security specialist migrating to Australia?

What is the role of an ICT security specialist migrating to Australia?
Protecting digital assets cannot be overstated in a world where technology guides business, communication, and innovation. Cyber threats are becoming more sophisticated, targeting individuals, organisations, and even governments. Whereas ICT security specialists are at the front lines of this digital defence. The hidden ones protect our systems, data, and networks from cyberattacks.
An ICT Security Specialist is a professional committed to protecting an organisation’s digital assets, networks, and systems from cyber threats. They are the first-line defenders against data breaches, malware attacks, and unauthorised access, considering that sensitive information remains confidential, systems remain functional, and businesses can operate securely.
What is an ICT security specialist?
An ICT Security Specialist is a highly skilled professional protecting an organisation’s information and communication technology (ICT) infrastructure. This infrastructure consists of networks, databases, hardware, software, and digital information. Their primary goal is to defend these critical systems from cyber threats such as hacking, malware, phishing, ransomware, and unauthorised access while ensuring sensitive data remains confidential, secure, and available.
They develop, enforce, and maintain security policies, ensuring observance of legal, regulatory, and industry standards, such as GDPR or ISO 27001. These professionals create and implement advanced security solutions, such as firewalls, encryption protocols, intrusion detection systems, and authentication mechanisms, to protect networks and applications from attacks.
In the event of a security breach, they lead the incident response process, investigating the root cause, mitigating the damage, and implementing strategies to prevent future occurrences.
Furthermore, they play a crucial role in promoting a culture of cybersecurity awareness within organisations by training staff on best practices and advancing threats.
By combining their expertise in ethical hacking, cryptography, and advanced cybersecurity tools, ICT Security Specialists contribute significantly to the resilience and operational continuity of businesses in an increasingly digital and interconnected world.
Learn more: Is it worth migrating to Australia for IT professions?🤔🤷✈️
Roles and Responsibilities of an ICT Security Specialist

An ICT security specialist plays a critical role in safeguarding an organisation’s information and communication technology systems. For professionals migrating to Australia, this role aligns with skill shortages in the country and is often listed on Australia’s Skilled Occupation Lists (e.g., Medium and Long-Term Strategic Skills List, MLTSSL). Here’s an overview of their responsibilities and opportunities:
Their primary roles and responsibilities are given below:
1. System Protection and Monitoring
You will design and implement advanced security systems to protect critical IT infrastructure, which may include cloud services, on-premise networks, and hybrid setups.
Your role involves continuously monitoring traffic for irregularities, detecting unauthorised access attempts, and ensuring system integrity through tools like firewalls, SIEM (Security Information and Event Management) systems, and intrusion prevention and detection software.
2. Risk Management
Australia is highly focused on cybersecurity due to increasing global threats and local regulations, so risk assessments are a priority.
This involves conducting penetration testing, evaluating the organisation’s existing defences, and suggesting actionable improvements to reduce risk levels.
As an ICT Security Specialist, you must provide guidance on strategic planning to protect sensitive data, particularly in sectors like banking, government, and healthcare.
3. Incident Response
You’ll need to act quickly and decisively during security incidents, such as ransomware attacks, data breaches, or DDoS (Distributed Denial of Service) attacks.
Your role may require coordinating with external agencies, such as the Australian Cyber Security Centre (ACSC), during major incidents.
4. Policy Development
In addition to protecting systems, you will help shape security policies tailored to Australian standards and laws.
This includes creating comprehensive data privacy policies aligned with frameworks like the Notifiable Data Breach (NDB) scheme, which mandates timely reporting of breaches affecting personal information.
5. Training and Awareness
ICT Security Specialists often educate staff on phishing risks, password management, and secure practices to reduce the likelihood of human error—a major factor in cyber incidents.
You may conduct simulation drills to enhance employee awareness.
6. Keeping updated with Threats
Cyber threats evolve rapidly, so your role requires continuous learning about the latest technologies, such as AI-driven security systems, blockchain applications for cybersecurity, and emerging malware trends.
Requirements to apply for PR
To apply for Permanent Residency (PR) as an ICT Security Specialist (ANZSCO Code 262112) in Australia, you need a minimum of 65 points under the points-based system, though higher points improve your chances in this competitive field.
Points are awarded based on various factors: age (up to 30 points, with the maximum for those aged 25–32), English proficiency (up to 20 points for IELTS 8.0 or equivalent), skilled employment experience (up to 20 points depending on years and location), and educational qualifications (up to 20 points for a doctorate or 15 for a bachelor’s or master’s degree).
Additional points for Australian study, regional study, specialist STEM education, partner skills, or state/territory nomination can be gained. For example, achieving superior English proficiency, accumulating relevant work experience, and securing state sponsorship can significantly boost your total.
With a competitive score above 65, you increase your likelihood of receiving an invitation to apply for PR.
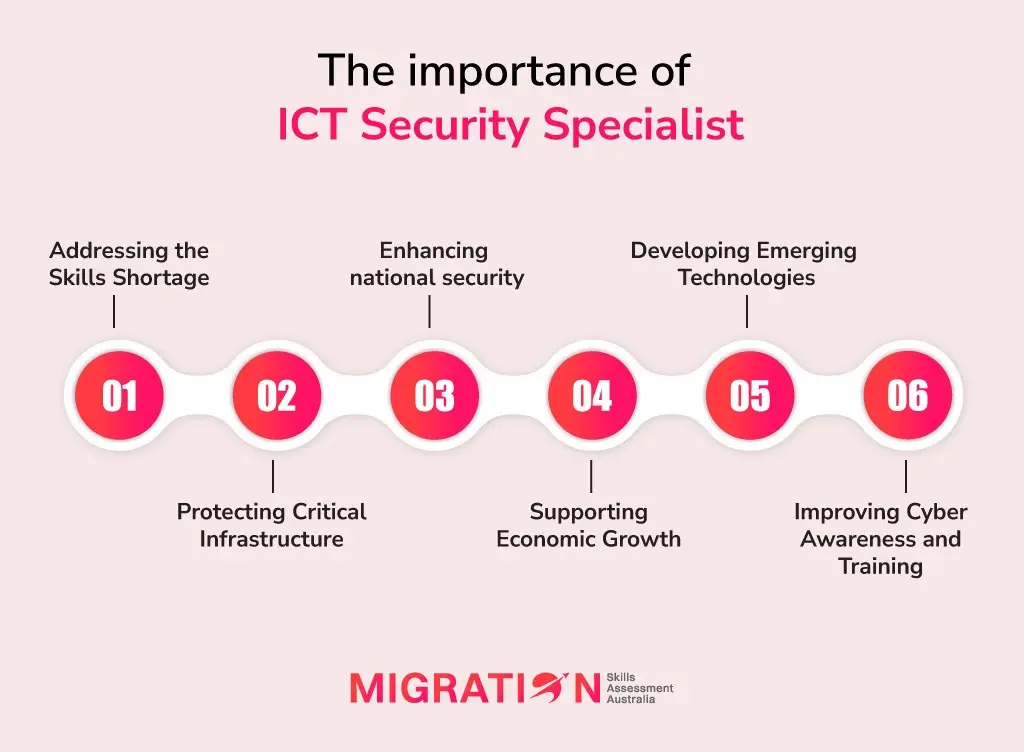
The importance of ICT Security Specialist
The migration of ICT security specialists to Australia is critical in addressing the country’s technological and security challenges. Here’s a more detailed explanation of why their presence is so important:
1. Addressing the Skills Shortage
Australia is experiencing a significant shortfall of skilled professionals in the cybersecurity domain. This gap poses risks to businesses and government entities that require robust digital protection. Migrating an ICT security specialist provides the expertise to
- Safeguard sensitive data and systems.
- Support industries struggling to find local talent with the right qualifications and experience.
- Build a more secure and efficient digital economy.
2. Protecting Critical Infrastructure
Cyber threats are evolving rapidly, targeting essential sectors such as healthcare, banking, telecommunications, and energy. These systems are vital for national well-being and economic stability. Specialists migrating to Australia contribute by:
- Designing advanced security frameworks for critical systems.
- Detecting, preventing, and responding to cyber incidents that could disrupt services or jeopardise safety.
3. Enhancing National Security
Australia faces increasing risks of cyberattacks from global adversaries. Cybersecurity is a key component of national defence strategies. Migrating ICT Security Specialists:
- Strengthen the nation’s capacity to detect and counteract cyber threats.
- Play a critical role in securing government systems and sensitive data.
- Help in protecting intellectual property and trade secrets from cyber espionage.
4. Supporting Economic Growth
A secure ICT infrastructure is foundational for economic development. Businesses are more likely to innovate and expand when they operate in a healthy digital environment. Migrating specialists:
- Ensure businesses can confidently adopt cloud computing, AI, and IoT technologies.
- Help prevent financial losses due to cybercrime, bolstering overall economic stability.
- Attract foreign investment by demonstrating Australia’s commitment to cybersecurity.
5. Developing Emerging Technologies
Innovations like the Internet of Things (IoT), artificial intelligence (AI), and blockchain depend on robust security measures to be widely adopted. ICT Security Specialists enable the safe integration of these technologies by:
- Addressing vulnerabilities specific to new tech.
- Promoting trust among users and developers, ensuring these technologies achieve their potential without security concerns.
6. Improving Cyber Awareness and Training
Migrating specialists bring a wealth of international experience and knowledge. They:
- Share best practices and cutting-edge techniques with local ICT professionals.
- Train and mentor the next generation of cybersecurity talent in Australia.
- Contribute to raising awareness about cyber risks and effective security practices across various sectors.
What are the ICT security specialist jobs?

The ICT security specialist jobs are extensive and continue to grow, especially as cybersecurity becomes an increasing priority for businesses, governments, and individuals. Cyber threats are evolving, and organisations are pursuing skilled professionals to protect their digital assets.
Below are some of the key career opportunities for ICT security specialists:
1. Security Analyst
A security analyst is typically an entry-level or mid-level position in the cybersecurity field. Security analysts are responsible for examining and inspecting an organisation’s security systems for potential threats, exposures, and weaknesses. They help to implement security measures, perform regular audits, and respond to security incidents.
Here are the skills required for a security analyst:
- Knowledge of network protocols, firewalls, and intrusion detection systems.
- Familiarity with SIEM tools (Security Information and Event Management).
- Strong problem-solving and analytical skills.
2. Network Security Engineer
A network security engineer is responsible for maintaining and securing an organisation’s network infrastructure. They design, implement, and manage security measures to protect the organisation’s network from cyberattacks, such as DDoS (Distributed Denial of Service) attacks, malware, and unauthorised access.
Skills Needed:
- Understanding of network security tools, such as firewalls and intrusion detection systems.
- Strong understanding of network protocols (TCP/IP, DNS, etc.).
- Experience with configuring VPNs and secure network designs.
3. Penetration Tester (Ethical Hacker)
A penetration tester, or ethical hacker, is hired to conduct controlled attacks on an organisation’s systems to identify vulnerabilities before malicious hackers can exploit them. They simulate real-world cyberattacks to assess the strength of the organisation’s security posture.
Skills Needed:
- Strong knowledge of hacking tools and techniques.
- Familiarity with vulnerability scanning and penetration testing tools.
- Expertise in programming and scripting languages (e.g., Python, Java, Bash).
4. Security Consultant
A security consultant is an expert who works with businesses to improve their overall cybersecurity posture. They assess an organisation’s security vulnerabilities, design security strategies, and implement best practices to protect sensitive data and prevent cyberattacks.
Skills Needed:
- Strong problem-solving and analytical skills.
- Expertise in cybersecurity regulations and standards.
- Excellent communication skills for working with clients and presenting findings.
5. Security Architect
A security architect is responsible for designing and building secure IT systems and networks. They create the security infrastructure that protects an organisation’s data and digital assets. This role is ideal for those who enjoy both strategic planning and technical implementation.
Skills Needed:
- In-depth knowledge of network design and architecture.
- Experience with firewalls, encryption, and access control technologies.
- Ability to create scalable, secure systems and networks.
6. Chief Information Security Officer (CISO)
The CISO is the highest-ranking executive responsible for an organisation’s overall cybersecurity strategy. They manage a team of security professionals, set policies, and oversee the implementation of security measures to protect the company’s digital assets. The role needs both deep professional knowledge and reliable leadership skills.
Skills Needed:
- Strong leadership and management skills.
- In-depth knowledge of cybersecurity trends, policies, and regulations.
- Experience with risk management and business continuity planning.
7. Cloud Security Engineer
As more organisations adopt cloud computing, the role of a cloud security engineer has become increasingly important. This specialist focuses on securing cloud infrastructure, applications, and data. They ensure that cloud-based systems are configured securely and are protected against data breaches and attacks.
Skills Needed:
- Knowledge of cloud platforms (AWS, Microsoft Azure, Google Cloud).
- Experience with cloud security tools and protocols.
- Familiarity with encryption, identity management, and access control in the cloud.
8. Incident Responder
An incident responder specialises in responding to security incidents, such as data breaches or cyberattacks. They are trained to quickly contain the damage, investigate the cause of the attack, and ensure that systems are restored to normal operations as quickly as possible.
Skills Needed:
- Knowledge of incident response frameworks and processes.
- Experience with forensic tools and techniques.
- Strong problem-solving and troubleshooting abilities.
What are the skills required for an ICT security specialist?

To become an ICT security specialist, individuals must maintain a combination of technical, analytical, and soft skills, along with relevant qualifications and certifications. Below is a detailed overview of the key skills required for a career in ICT security.
1. Technical Skills
a. Network Security
Understanding how to protect networks from cyber threats is essential. This includes knowledge of firewalls, VPNs, intrusion detection/prevention systems (IDS/IPS), and secure network architecture.
b. Operating Systems Knowledge
ICT security specialists must be proficient in both Windows and Linux/Unix operating systems, as attackers often target vulnerabilities in these systems.
c. Cryptography
A strong understanding of encryption protocols (AES, RSA, etc.), key management, and secure communication protocols (TLS, SSL) is crucial for safeguarding data.
d. Security Tools and Software
Familiarity with security tools such as antivirus software, vulnerability scanners (e.g., Nessus, OpenVAS), and SIEM (Security Information and Event Management) tools like Splunk and SolarWinds is important for monitoring and defending systems.
e. Penetration Testing & Ethical Hacking
Knowledge of ethical hacking techniques and tools such as Metasploit, Nmap, Burp Suite, and Wireshark is essential for identifying and fixing vulnerabilities in systems and networks.
f. Incident Response & Forensics
ICT Security Specialists need the skills to respond quickly and efficiently to security incidents. This includes forensic analysis to trace and investigate the source of attacks.
g. Malware Analysis
A solid understanding of how malware works, including viruses, trojans, ransomware, and spyware, and the ability to identify, analyse, and remove malware.
h. Cloud Security
With the rise of cloud computing, knowledge of cloud security best practices, particularly for platforms like AWS, Microsoft Azure, and Google Cloud, is crucial for securing cloud environments.
2. Analytical Skills
a. Risk Assessment
Security specialists must be able to conduct risk assessments to identify vulnerabilities and weaknesses in an organisation’s infrastructure and understand how attackers may exploit them.
b. Threat intelligence
To effectively identify potential security risks, you must be able to collect, analyse, and interpret threat data.
c. Problem-Solving
ICT security specialists must quickly analyse and resolve security issues, often under pressure, requiring creative problem-solving skills.
3. Soft Skills
a. Attention to Detail
Cybersecurity professionals must spot even the smallest signs of potential threats or vulnerabilities. A keen attention to detail is vital for ensuring the security of systems and networks.
b. Communication Skills
Strong verbal and written communication skills are essential for collaborating with IT teams, presenting findings to management, and educating staff on security practices.
c. Teamwork
Security professionals often work as part of a team, requiring the ability to collaborate with colleagues across departments, including IT, compliance, and risk management.
d. Adaptability
The cybersecurity landscape is constantly evolving. Professionals in this field must be adaptable and eager to learn new tools, techniques, and trends to stay ahead of emerging threats.
e. Decision Making
Given the critical nature of their work, security specialists must make timely and informed decisions, often under stressful circumstances, such as during security breaches or attacks.
Conclusion
ICT security specialists are the unacknowledged heroes of the digital world. Their work ensures that our online transactions, business operations, and personal data remain secure in the face of constant threats. As technology advances, these professionals’ importance will only grow.
Whether you’re considering a career in cybersecurity or simply want to understand how organisations protect themselves, it’s clear that ICT security specialists are vital to the stability of the modern digital age. By combining technical expertise with strategic thinking, they stand as the last line of defence against the ever-evolving threats of the cyber landscape.
Moreover, the role of an ICT security specialist extends beyond just reacting to incidents. They also help shape the organisation’s overall security culture. Through training programmes, awareness campaigns, and regular security audits, they ensure that all employees are equipped to recognise and prevent potential risks, making security a shared responsibility across the organisation.
FAQs
1. Is ICT a good career choice?
ICT is an excellent choice for those who are passionate about technology and interested in solving complex problems.
2. What are the differences between ICT and cyber security?
ICT refers to all technology used for communication and information processing, including networks, hardware, and software.
Cybersecurity is a subset of ICT focused on protecting systems and data from cyber threats like hacking and malware.
ICT provides the technology, while cybersecurity ensures its safety from digital attacks.
3. What qualifications are required for an ICT?
For an ICT, you need:
- Education: high school, bachelor’s, or master’s degree depending on the role.
- Certifications: CompTIA A+, CCNA, MCSE, CISSP, AWS.
- Skills: technical, problem-solving, communication, and project management.
- Experience: internships or entry-level jobs.
- Training: Optional in cloud computing, software development, or cybersecurity.
4. What can be an example of an ICT?
Examples of ICT include:
- Computers and Servers
- Networks
- Smartphones and Tablets
- IoT Devices
5. Why is ICT security important?
ICT security is essential because it protects digital systems, data, and communication networks that individuals, corporations, and governments depend on daily.
6. What are the principles of ICT security?
The initial principles of ICT security are fundamental guidelines designed to protect information, systems, and networks from threats. They are as follows:
- Confidentiality
- Integrity
- Availability
- Security by Design
- Resilience
- Regular Updates and Patching